Our "face" is in desperate need of protection.
On October 26, the "Hangzhou City Property Management Regulations (Revised Draft)" was submitted to the Standing Committee of the 13th Hangzhou People's Congress for deliberation. The draft stipulates that property service providers shall not force owners to use shared facilities and equipment through fingerprints or face recognition and other biological information methods.
As one of the biological characteristics of the human body, face information, like fingerprints and iris, has become a means to prove one's identity. Face recognition technology, which performs identity verification based on human facial features, has been widely used, such as mobile phone unlocking, registration verification of various APPs, and lending.
However, in the era of personal information streaking, your "face" can also become a commodity to be bought and sold, and it is not valuable. A few days ago, according to CCTV reports, a large number of photos and other facial information are being privately traded. On the Internet, you can buy thousands of photos of face information for only 2 yuan.
The leak of individual face photos may not pose any threat to individuals. However, when using technical tools such as "photo activation", face photos can also achieve simple actions such as blinking and nodding. A large number of stolen face information, coupled with other leaked personal information such as ID card numbers and mobile phone numbers, has brought greater information security risks.
Recently, the APP Special Governance Working Group established by the National Information Security Standardization Technical Committee and others released a "Face Recognition Application Public Survey Report 2020" stating that 90% of the respondents have used face recognition, and 60% believe that people Face recognition tends to be abused, and 30% said that personal privacy or property security has suffered losses due to this.
But this is only the tip of the iceberg in the underground chain of black production of personal information data. Many more people may not know how much information they have stolen and what they have been used for.
Where do thousands of "faces" come from?
How much is a person's "face" worth?
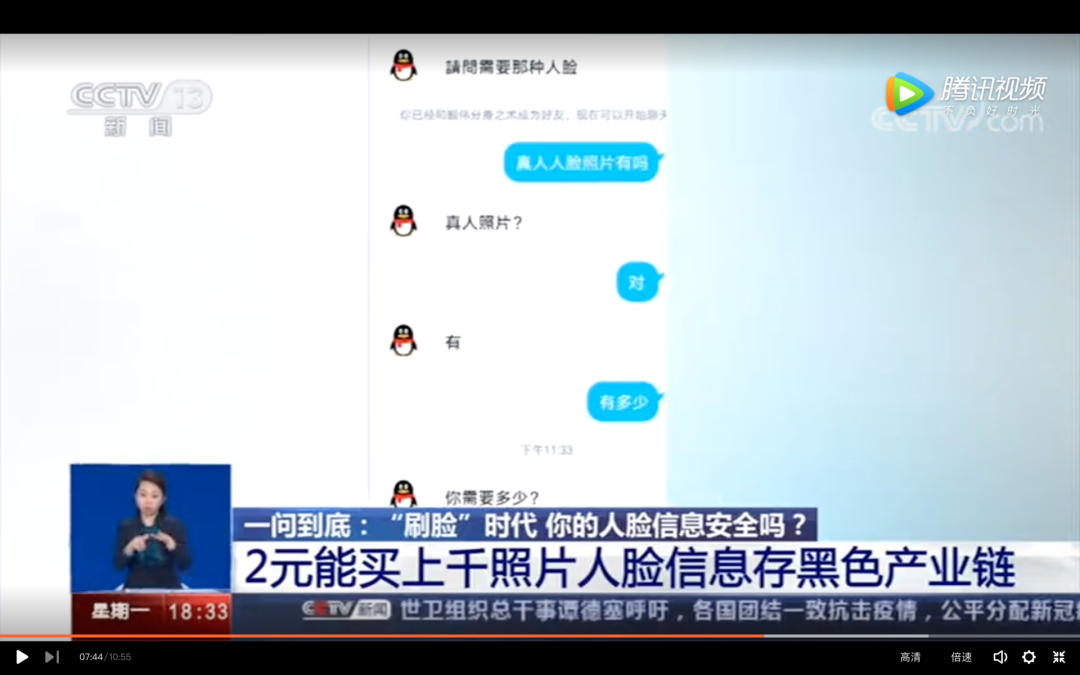
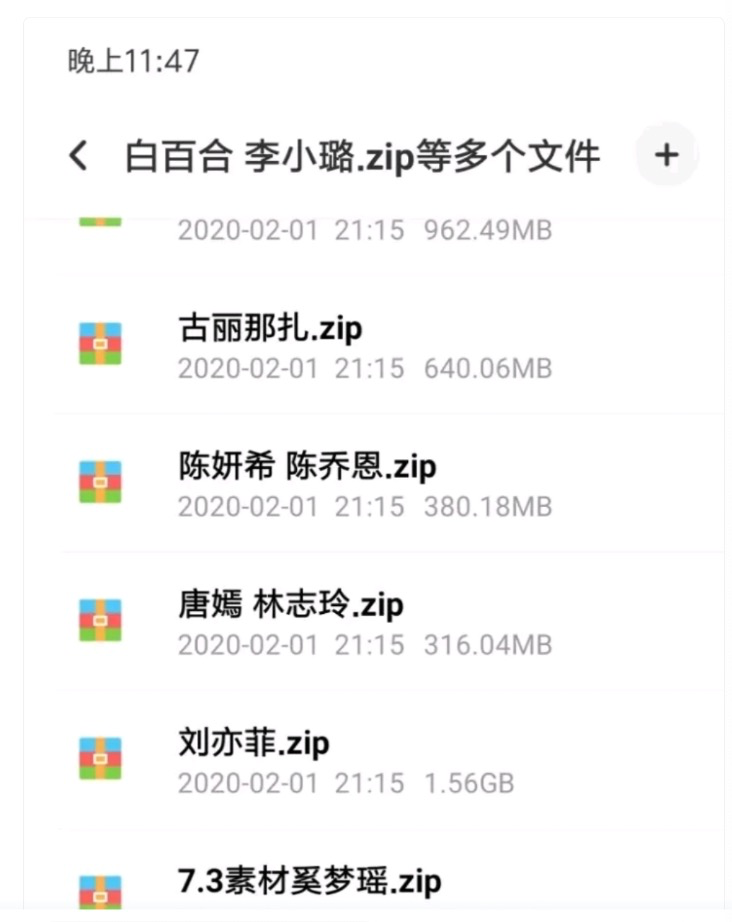
According to CCTV reports, on the online trading platform, you can buy thousands of face photos for only 2 yuan, and the price of 5,000 face photos is less than 10 yuan. In the photo libraries of these so-called "businesses" are private photos of real people, such as selfies and life photos. When a CCTV reporter asked the customer service whether the pictures involved copyright, the customer service denied it, but could not provide any material that could prove the copyright of the photo.
Photo/ Screenshot of CCTV report Ran Caijing
In July of this year, Ran Caijing also joined a QQ group called the "Face Technology Group Learning Group", which was filled with various "WeChat unblocking, replacing faces", "selling three-color face technology", "On behalf of registration" and other advertisements. After adding a friend with a netizen in the group, the other party claimed that a piece of information was priced at 3 yuan, including face and identity information, and then sent a lady's ID card information as verification.
According to previous reports by Xinhua News Agency, on online trading platforms such as Taobao and Xianyu, you can find shops that specialize in facial data and "photo activation" tools by searching for specific keywords.
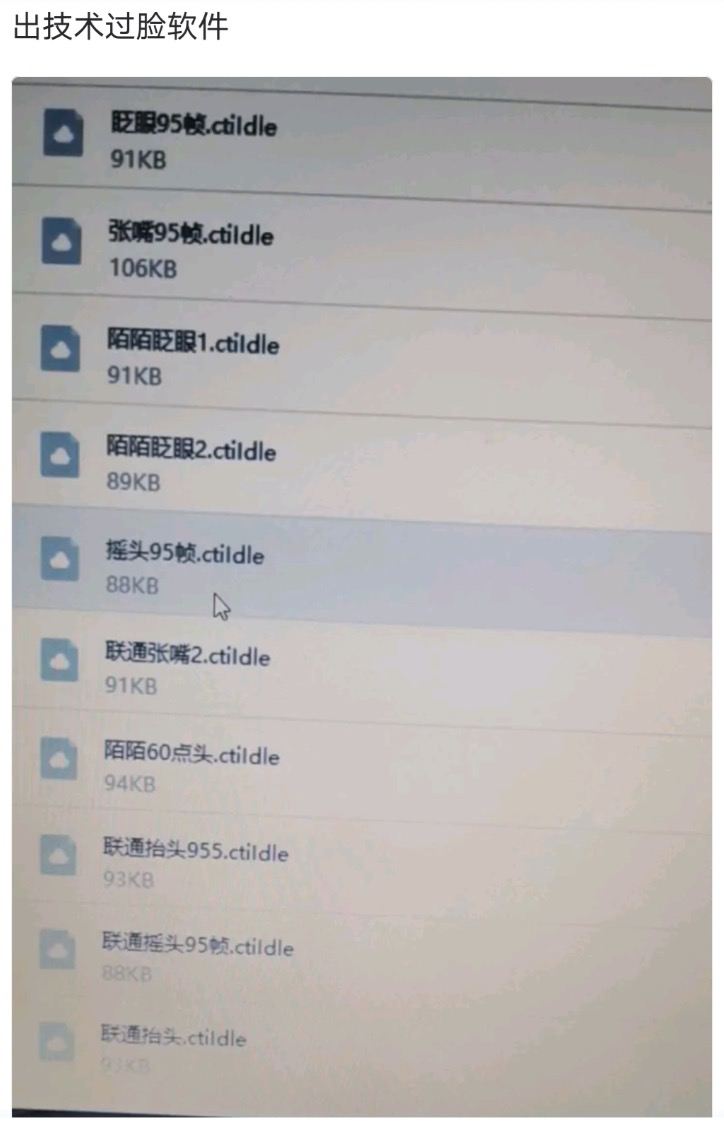
The so-called photo activation refers to the use of software tools to modify the face photo into a face verification video that can perform operations such as "blink, open mouth, and nod".
"Most Internet users don't have any privacy in front of some people." A "white guest" once said on Zhihu.
Where does the identity authentication information come from? "There are many source channels." An insider of a security vendor told Ran Caijing. For example, he said, for example, fortune-telling games that were once popular on WeChat, fortune-telling for free after uploading photos, in fact, some are made by black and gray products for the purpose of obtaining face data.
At the same time, some apps currently have excessive acquisition of user information. For example, the authorization information is used to obtain the user's camera and photo album permissions. In this way, a part of face information data will be obtained. On social media, life photos, selfies, etc. uploaded by users have also become the targets of black and gray products, which are obtained manually or by crawling means.
An employee in the security industry revealed that in his hometown in third- and fourth-tier cities, he saw salespeople in some communities or supermarkets distributing eggs, cooking oil and other commodities. "As long as you register your mobile phone number, it means it is voluntary." Some passers-by who can't help the temptation of free products deliberately register with obscured mobile phone numbers when receiving them, thinking that this is foolproof. But what they don't know is that in order to cope with the "face-brushing" and live-body detection on different application platforms, a new "face-passing industry" has emerged. To a large extent, these consumers have become the target of use. "When users register, their photos and dynamic videos have been collected by the hidden camera equipment." He said that the cost of obtaining these facial information is only a few eggs.
He Yanzhe, deputy director of the Evaluation Laboratory of the China Institute of Electronic Technology Standardization, said in an interview that if you only collect personal facial information without obtaining other identity information, the risk of privacy leakage is not too large. However, the personal data currently sold includes not only facial data such as photos, but also a series of private data such as personal mobile phone numbers, social media accounts and even ID numbers and bank card numbers.
"In recent years, the proportion of data breaches originating from corporate'internal ghosts' is gradually increasing." An industry insider said. Caijing once reported that 80% of data breaches were caused by internal employees. Almost all areas where user funds and core privacy data are relatively concentrated, whether it is financial insurance, industry and commerce, entertainment, telecom operations, or consumer industries such as medical care, food delivery, hotels, etc., in the production link at the bottom of the data, the data of black production is "transported" "Work" is everywhere.
In May of this year, the police in Huai'an City, Jiangsu Province cracked a case involving a certain employee of China Construction Bank selling user information data. The relevant bank employees will use the identity card information, or even to pay the balance of catchy record, etc. sold to a black home birth, within a year of personal income over 300,000 yuan profit. In the data trafficking industry chain involved in this case, more than 50,000 pieces of personal information data of citizens were involved, and the amount involved was more than 20 million yuan. Regarding the case, as early as June 2019, the police noticed that someone was selling bank card-related information through communication tools such as QQ, and claimed that only the bank card number or ID number was required to inquire about the bank card user’s All identity information and transaction records, etc.
As early as the beginning of 2017, CCTV also exposed a data breach that contained 5 billion pieces of citizen data, many of which came from JD.com. According to the police report, the suspect was an internal network engineer from the JD Network Security Department who had colluded with a data vendor who had stolen personal information to "guard and steal."
According to various relevant case information on the Chinese Judgment Documents online, it can be seen that the perpetrators who reselled the information cost only a few yuan per piece of information. In 2018, in an information trafficking case in Tianjin, 380,000 pieces of personal information of citizens were sold, and the profit was only 7,200 yuan. In calculation, each piece of information is only a few cents.
Han Haosheng, a senior security analyst at 360 Cyber Security Response Center, once revealed that most users often use "a set of passwords to walk the world" for convenience, but this also provides great convenience for black and gray products. Hackers use a large number of leaked user social software and mailbox accounts, etc., to build dictionary tables, and use software to try to log in batches on different websites continuously. This is "crash library".
This means that as long as hackers get the information leaked on one platform and try on other websites, they can "crush" out more account information on the target website.
Through various channels, these leaked data, in addition to being sold, have also accumulated into a structured database of hackers, that is, the "social work library." Face information, coupled with various other personal identification information leaked, these comprehensive social work database data provide a data basis for various black and gray products involving false information transactions.
What is "face" used for?
In the sale of "A i change the face" of software in the hands of businesses, often providing a bunch of star video list, include the well-known actress in a second-tier, any customer choice. Of course, these are not real celebrity videos, but the result of "face changing" processing.
A screenshot of the list of actress videos released by an AI face-changing "merchant"
AI face swap technology has been accompanied by controversy since its emergence. Although it provides convenience to the film and television industry, it also provides "business opportunities" for some people: some erotic videos are packaged and sold after face replacement, and the face replacement is natural. It is the well-known actress that is more popular.
A year ago, the face-changing software "ZAO" exploded. Users only need to upload a photo in the APP to replace it with various characters, whether it is "Little Plum", Monroe or Chow Yun-fat. But what it makes the public perceive is not only the magic of "AI face-changing", but also the scary thing: how will these uploaded photo information be processed? Once someone uses this technology to generate a few real videos and publish false information, how much hidden danger will it cause to the legitimate rights and interests of individuals and public safety? As a result, three days after ZAO went online, it went from ranking second in the APP Store to being interviewed by relevant departments and then being removed.
But in fact, a set of AI black production chains on face recognition data has long existed and taken shape, and AI face-changing is only one branch of it.
The ID card photos required for registration and authentication on different network platforms or APP applications can be collected in various ways. With the increasing maturity of face recognition technology, living body detection is becoming the main verification method for registration in the Internet fields such as finance and telecommunications. As a result, in order to deal with "face-swiping" on different application platforms, a business called "face-to-face" has been born.
Several people in the security industry have revealed that using tools such as PS, you can create a face map with background, and then use dynamic video software to complete simple blinking and other actions to generate a video.
Ran Caijing found through searches on online platforms such as Tieba that there are still posts peddling "AI face changing tutorial" and "face technology software". The seller’s QQ account also provides an introduction to the relevant “business”. The objects that can be registered on “Cross-face” include 58.com, Zhaolian Recruitment and other platforms; or can provide photos to unblock the frozen WeChat and Alipay accounts, etc. .
A screenshot of Burning Finance posted on a platform that sold facial software
Not long ago, Xinhua News Agency also reported that some cybercriminals used e-commerce platforms to sell illegally obtained personal faces and other identity information, as well as "photo activation" online tools and tutorials. On online trading platforms such as Taobao and Xianyu, by searching for specific keywords, you can find shops that sell face data and "photo activation" tools. "A set of ('photo activation') software plus tutorial is 35 yuan, you pay directly, and I will send you the link after confirming the receipt." A Xianyu seller said when using voice negotiation in Xianyu's dialog box.
Earlier, "Weekend of the Rule of Law" disclosed the operation process of cracking the face recognition of a payment APP. As long as you have “high-quality materials” (one-handed high-definition static frontal portrait photo, ID card front and back photo), as well as a facial technology flashing package and an ordinary Xiaomi mobile phone, flashing and downloading tools, you can create live dynamics Face video; at the same time, the background system grabs scripts, reads files, and matches the dynamic face recognition of the APP to succeed.
In the CCTV report, a mask can replace a human face to unlock. After the researchers put a mask on the opposite side of the phone, they adjusted the light, color temperature, and angle of the mask. After several comparisons, the phone was successfully unlocked. Experts said that the cost of making the mask is not high, and 3D printing technology can produce a face mask or headgear with acceptable accuracy, as long as it is not in a very dark or bright background, through the mask or headgear for face recognition The success rate is as high as 30%.
In the chain of face recognition black production, only the downstream provides various personal data information. Based on it, individuals or small studios that provide technical services provide software and services such as facial activation and face-passing. . At the uppermost level, there are people who use this type of information and technology to "monetize" people, including marketing, scalping, and even financial and telecom fraud. This type of data with facial information can even be used for money laundering, hacking and bring lawsuits to the photo owner.
According to CCTV reports, on August 13 this year, the public security department of Hangzhou Qiantang New District arrested two suspects who had stolen personal information. They defrauded the platform's face recognition through technical means and stole thousands of them on multiple online platforms. The personal information of a platform account was prepared to be resold at a price of 80-100 yuan per order, but was caught by the police before the transaction could be made.
At the beginning of this year, a criminal ruling issued by Zhejiang Quzhou Intermediate People’s Court disclosed that Zhang, Yu and others used technical means to deceive Alipay’s face recognition authentication, and used citizens’ personal information to register Alipay accounts, and illegally earned tens of thousands of yuan. He was eventually sentenced for the crime of infringing on citizens' personal information.
According to the police, in the above two cases, the suspects used AI face-changing technology to illegally obtain citizen photos. After certain preprocessing, they generated dynamic videos through photo activation software, deceiving the face verification mechanism. Afterwards, log in to various network service platforms through private social platform accounts purchased in batches online, register members or conduct real-name authentication.
In November 2019, the People’s Court of Jiangshan City, Zhejiang Province ruled on a case of infringement of citizens’ personal information. The reason for the case is that one of the Alipay promotion policies is that when old users introduce new users to register for Alipay, old users can get a promotion bonus of 28 yuan. , A scam team collected thousands of people’s photo information and used these photos to make movable 3D videos to register for Alipay accounts to make money. A total of thousands of accounts were successfully registered, and a total of 30324 yuan was illegally profited.
In response, Alipay responded to the media saying that in 2018, the Alipay security system detected abnormal behaviors in opening accounts with facial recognition for identity authentication, promptly reported to the police, and upgraded the anti-attack technology for facial recognition authentication.
Behind the data breach, there are also more hidden dangers.
The industry has been discussing the safety of online car-hailing business for several years, and on some social platforms, there are still accounts asking how to "pass face" on the Didi platform.
At the beginning of 2018, the Guangdong police announced the black property case of registering fake Didi accounts, including hundreds of thousands of accounts and seizing more than 200,000 pieces of illegally obtained citizens' personal information. In January 2019, a fraud case of "black production generation calling" was solved in Guangdong. The black industry intermediary that provides the "car-hailing" service registered a platform account and used the purchased ID card, mobile phone number and Alipay account to bind it. Subsequently, using these accounts, the intermediary solicited customers to book a car at a preferential price, refused to pay the platform and driver fares after the transaction, and immediately abandoned the original account after one or two transactions. According to the police report, the loss verified by the platform reached 4 million yuan.
In fact, the illegitimate intention of personal identity data leakage, including face data, has become a fairly "refined" industrial chain. The huge amount of citizen information gathered from hacker attacks, database crashes, crawlers and other channels will be separated, deduplicated, screened, and sorted by various intermediaries after the gathering, that is, "washing the database." With this type of data that has been tagged and sorted, the registration information of users on more platforms is also accurately linked. At this time, the data price is different from the "wholesale price" of a few cents in the early stage, and it has begun to rise. According to industry sources, about 10,000 pieces of ordinary data can be sold for several hundred yuan, while the price of processed information with more detailed data can increase by tens or even hundreds of times.
This type of data is then almost sold to various types of "buyers" in a "customized" manner. Telecom fraud is one of the most important buyers of such data. In the Xu Yuyu fraud case that caused a national sensation in 2016, the fraudsters purchased 1,800 high school graduate data through QQ groups. Ordinary consumer data can be sold to different retail industries for precise sales.
Financial identity and account information, including bank cards, online banking, stocks and other information, as well as virtual currency and game realizable accounts, can be directly realized or sold to financial fraudsters. With more detailed user identification information, personal assets and other related data, it can be sold to online lending intermediaries to handle online loans or implement precision fraud.
On Weibo , a user said that his friend had encountered credit fraud. An illegal intermediary said that his university roommate borrowed her identity to borrow an online loan, and provided relevant identity information to win her trust, thereby defrauding her. It cost about 100,000 yuan.
"Face Recognition Application Public Survey Report (2020)" In order to understand the use of face recognition and the public’s security feelings, ten types of face recognition scenarios are listed, including payment and transfer, account opening and cancellation, real-name registration, unlocking, decryption, and exchange. After collecting more than 20,000 anonymous questionnaires, such as face entertainment, government services, traffic security inspection, access control and attendance, campus/online education, and public safety supervision, it was found that the management efficiency improvement brought by face recognition is the promotion of technology in various industries. However, in terms of safety perception, the scores given by respondents were significantly lower. Sixty percent of respondents believe that face recognition technology has a tendency to abuse, and thirty percent said that they have suffered privacy or property losses due to the leakage or abuse of facial information.
Who will govern face recognition
The domestic "face recognition first case" opened in June this year. In October last year, Guo Bing, an associate professor at Zhejiang Sci-Tech University, filed a lawsuit because he refused to accept the way that Hangzhou Wildlife Park requires facial recognition to enter the park. He believes that this is a struggle against the current "abuse of face recognition technology."
In March of this year, Tsinghua University Law School professor Lao Dongyan discovered that the community where she lived had posted an announcement on the installation of a face recognition access control system, asking the owner to provide real estate certificates, ID cards, face recognition and other information. She posted the report and legal basis on the risks of face recognition to two WeChat groups each with hundreds of owners, but did not get the expected response. Lao Dongyan also sent a legal letter to the neighborhood committee and the property, and later there was a four-party "negotiation" between her as the owner and the street, the property committee and the property. The street finally agreed that the owner can voluntarily choose the method of access control card, mobile phone or face recognition when entering and leaving the community.
"I just struggled a little bit." Lao Dongyan said at a seminar on "abuse of human biological information collection and its legal rules" in September this year. She believes that the popularization and application of face recognition itself will bring "incalculable risks" to the public's personal and property safety. "The problem is that we may no longer enjoy any privacy, and therefore lose most of the privacy. Safety."
Through the "first case of face recognition," the law is also expected to set the boundaries for the application of technology. "Is it reasonable to force citizens to accept face recognition? The final judgment will be of exemplary significance throughout the country." Lao Dongyan said in an interview with Nanfang Daily.
The "Hangzhou City Property Management Regulations (Revised Draft)" took the first step. If passed, it will become the first formal legislation in the country to regulate facial recognition in communities.
The development of any technology is accompanied by risks, and it also places new demands on supervision and government governance.
In 2017, the "Cyber Security Law" was promulgated, and the judicial interpretation clearly stipulates 10 types of criminalization, including illegal acquisition, sale or provision of track information, communication content, credit information, and property information; more than 50 items are illegal; acquire, sell or provide accommodation information, communications records, health physiological information, pay easecredit information other that may affect the personal and property safety of citizens and other personal information of more than 500.
However, Tencent also pointed out in the "Internet Account Malicious Registration of Black Industry Governance Report" released in 2018 that malicious registration of accounts is becoming a security risk control for Internet companies in scenarios such as finance, e-commerce, life services, social networking, and content. Focus. However, there is no direct provision in the current law for malicious registration. Therefore, a large number of illegal workers wandered in this gray area and avoided criminal responsibility.
According to CCTV reports, due to the variety of face recognition applications and there is no uniform industry standard, a large amount of data is stored in the central database of each application operator or technology provider. The desensitization, security and purpose of the data are unknown to the outside world. Once the server is compromised, the face data will be exposed to the risk of leakage.
China Consumer Association has issued "APP 100 models of personal information collection sets and Privacy Policy Assessment Report", paragraph 100 of which the evaluation of APP, there are 10 models APP alleged excessive collection of personal biometric information.
The new version of the "Information Security Technology Personal Information Security Specification" implemented on October 1 clearly states that before collecting personal biometric information such as faces and fingerprints, personal information subjects should be separately notified of the purpose and purpose of collecting and using personal biometric information. The method, scope and storage time and other rules shall be obtained with the express consent of the personal information subject. Currently, the "Personal Information Protection Law of the People's Republic of China (Draft)" is also seeking public opinions from the public. The draft proposes that the installation of image collection and personal identification equipment in public places should be necessary to maintain public safety, comply with relevant national regulations, and set up prominent reminders.
In any case, as a special personal privacy information, "Face" deserves everyone's attention for its data security. "Face data is irreplaceable because we cannot change faces. Once leaked, it will be leaked for life. Even if legal measures are taken to successfully defend rights, it will be difficult to restore it to the original state." At the seminar in September, Lao Dongyan said.
No comments:
Post a Comment